 Search
Search


The Financial Crimes Enforcement Network (FinCEN) released a comprehensive Financial Trend Analysis (FTA) focused on information pertaining to identity-related suspicious activities within Suspicious Activity Reports (SARs) filed during the calendar year 2021.1 According to FinCEN, 1.6 million reports, constituting 42% of the filings for the year 2021, were associated with identity-related concerns. These reports amounted to a staggering $212 billion in suspicious activity.
The instances of identity-related SARs demonstrate a consistent upward trend.2 The FTA report scrutinizes suspicious activities linked to the exploitation of identity processes, encompassing account creation, account access, and transaction processing (collectively, identity processes). The report specifically underscores details pertinent to depository institutions and money services businesses (MSBs).
On January 9, 2024, FinCEN issued an FTA on information linked to identity-related suspicious activity that identified more than 14 typologies commonly specified in identity-related BSA reports. The top five typologies constituted 88% of identity-related SARs and 74% of the total suspicious activity amount in the reported calendar year 2021, as illustrated in the graph below:
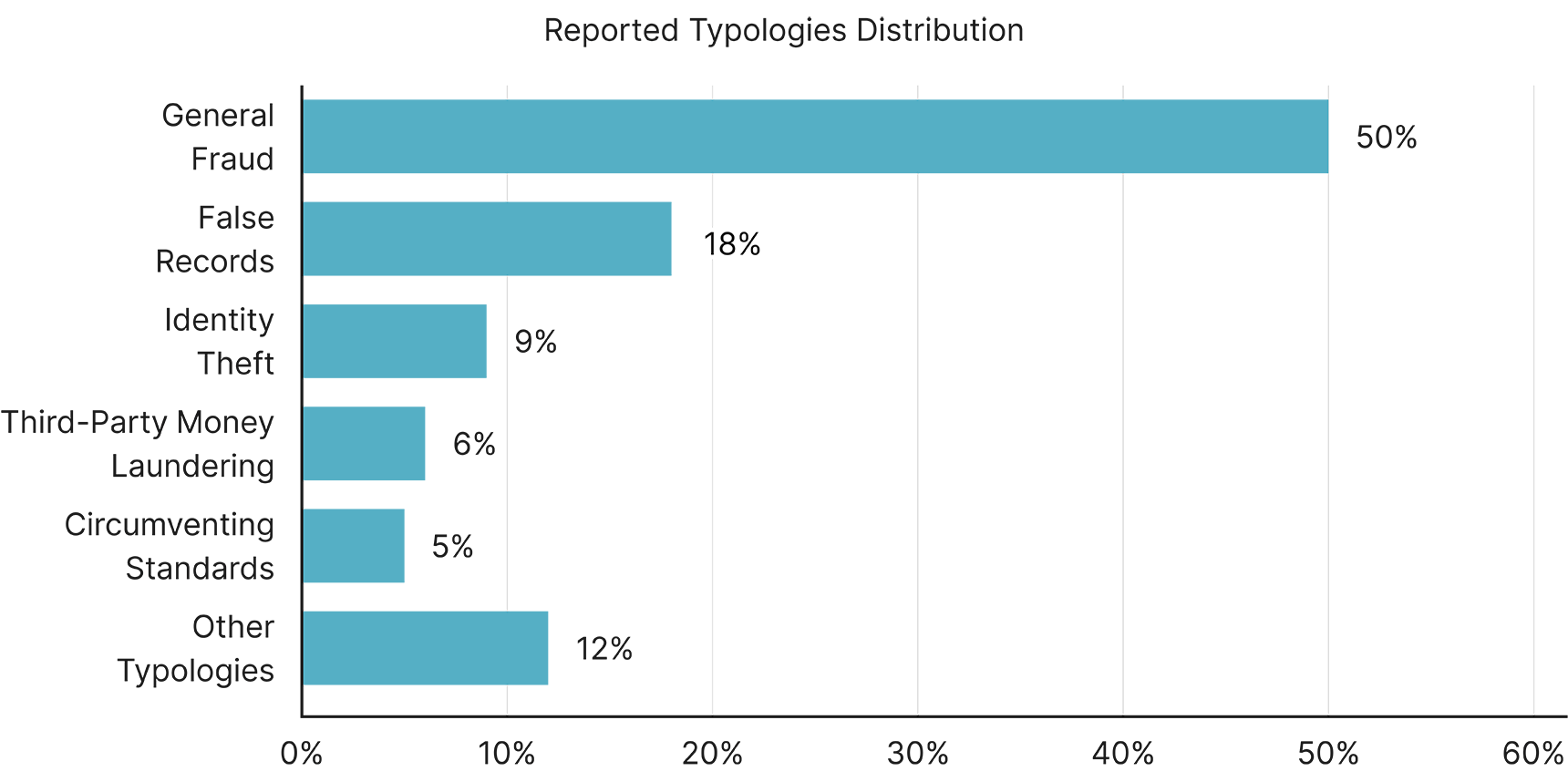
General Fraud — General fraud was the most frequently reported concern in SARs, echoing known overarching trends that warranted the inclusion of fraud into the national Anti-Money Laundering/Counter-Financing of Terrorism (AML/CFT) priorities.3 Notably, the FTA report accentuates the escalating threat posed by imposter scams, resulting in reported losses exceeding $2.6 billion in 2022.
False Records — This typology involves attackers providing false identification, documentation, and payments in interactions with financial institutions (e.g., fake Social Security numbers). Some financial institutions proactively identify false records, while others only identify concerns after the fact. False records are an especially pernicious problem for digital financial products and institutions, as predominantly physical forms of identification are more difficult to verify without the opportunity to review in person.
Identity Theft — Attackers exploit compromised personal identifying information (PII) to open accounts and apply for credit lines4 without the rightful owner's permission (e.g., victim is deceased, incarcerated, or otherwise unable to apply). For example, factors contributing to this typology include large-scale data breaches, such as the 2017 Equifax breach that exposed the personal information of 147 million Americans.5
Third-Party Money Laundering (TPML) — This includes individuals acting as intermediaries (straw buyers and money mules) to conduct transactions on behalf of others. The FTA report outlines it entails the recruitment of money mules online through scams, making them witting or unwitting participants in laundering fraud proceeds while also concealing the identity of the true transactor, thereby circumventing verification.
Circumventing Standards — Directly tied to the lack of proper recordkeeping or registration by financial institutions, where circumventing standards may lead to failures in customer and counterparty verification.
Identity-related exploitation involves three distinct tactics—"impersonation," "compromise," and "circumvention"—occurring in the identity processes of validation,6 authentication,7 and verification,8 respectively.
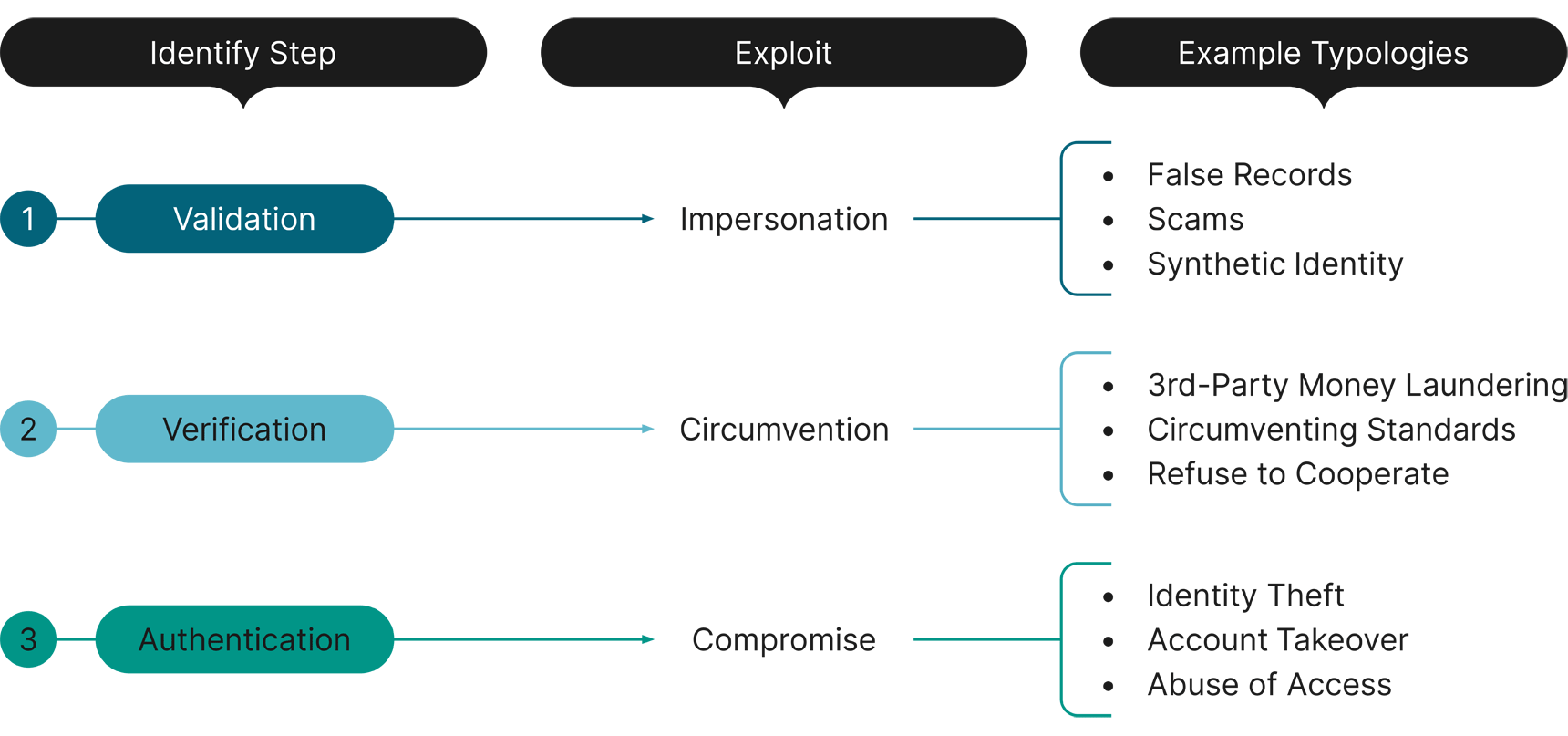
Identity-related suspicious activity trends exhibit variations across financial institutions. Specifically, MSBs report circumvention of verification as the primary cause of identity exploitation. Depository institutions, along with the broader financial services entities, grapple predominantly with impersonation challenges that exploit the lag in traditional, government-issued identification methods in a rapidly digitizing world. FinCEN emphasizes the potential role of government-issued digital identification and increased public-private cooperation in closing this gap9 and addressing the multifaceted challenges posed by identity-related crimes.
Financial institutions should scrutinize their existing policies, procedures, and controls concerning the validation, authentication, and verification of customers' information. This entails a meticulous review to ensure alignment with evolving industry standards and the dynamic landscape of fraud.
In addition, financial institutions would benefit from a proactive stance that includes a comprehensive assessment of their exposure to fraud risks from products, services, customer base, and similar factors, plus identification and review of the existing mitigating measures.
Guidehouse can help financial institutions assess their fraud risk exposure, enhance fraud risk management programs, and improve fraud controls aligned to the identified trends. Areas of relevant expertise include:
Guidehouse can assess your fraud risk management program to determine whether it is effective, identify gaps or weaknesses, or conduct training on fraud compliance. Guidehouse is well-equipped to make an individualized assessment of your unique circumstances and offer innovative advice and solutions for responding to heightened identity-related fraud risks.
1. Review of Identity Related Suspicious Activity 2021 Threats and Trends. 2024. Fincen.gov. Washington D.C.: Financial Crimes Enforcement Network. https://www.fincen.gov/sites/default/files/shared/FTA_Identity_Final508.pdf.
2. Federal Trade Commission. “Consumer Sentinel Network Data Book 2022.” Ftc.gov. Washington D.C.: Federal Trade Commission, February 2023. https://www.ftc.gov/system/files/ftc_gov/pdf/CSN-Data-Book-2022.pdf.
3. “Financial Crimes Enforcement Network Anti-Money Laundering and Countering the Financing of Terrorism National Priorities.” 2021. https://www.fincen.gov/sites/default/files/shared/AML_CFT%20Priorities%20(June%2030%2C%202021).pdf.
4. “Identity Theft Trends, Patterns, and Typologies Based on Suspicious Activity Reports.” 2005. https://www.fincen.gov/sites/default/files/shared/ID%20Theft%2011_508%20FINAL.pdf.
5. Federal Trade Commission. “Equifax Data Breach Settlement,” December 2022. https://www.ftc.gov/enforcement/refunds/equifax-data-breach-settlement.
6. The validation stage begins when a customer presents identity attributes and supporting evidence (e.g., birth certificate, passport, driver’s license, etc.)—in person or remotely—for review by a financial institution. The financial institution makes these determinations by comparing the presented information and evidence against authoritative government data.
7. In the authentication stage, a financial institution attempts to assess whether the customer is who they purport to be based on the customer’s possession and control of valid authenticators. Authentication provides risk-based assurance that the customer is the same customer whose identity was validated and verified during previous steps of the identity process.
8. In the verification stage, the financial institution confirms that the previously validated identity evidence belongs to the customer (e.g., matching the customer’s appearance to a photo on the customer’s photo identification documents). Verification tools and techniques can rely on humans or be entirely automated.
9. Kirby, Jimmy. “Prepared Remarks of FinCEN Acting Deputy Director Jimmy Kirby.” Presented at the Identity, Authentication, and the Road Ahead, a Cybersecurity Policy Forum, January 25, 2023. https://www.fincen.gov/news/speeches/prepared-remarks-fincen-acting-deputy-director-jimmy-kirby-during-identity-policy.
10. https://www.ftc.gov/legal-library/browse/statutes/fair-accurate-credit-transactions-act-2003
11. Reference the rule
12. “Payments App Zelle Begins Refunds for Imposter Scams after Washington Pressure,” reuters.com, n.d., https://www.reuters.com/technology/cybersecurity/payments-app-zelle-begins-refunds-imposter-scams-after-washington-pressure-2023-11-13/
Guidehouse is a global AI-led professional services firm delivering advisory, technology, and managed services to the commercial and government sectors. With an integrated business technology approach, Guidehouse drives efficiency and resilience in the healthcare, financial services, energy, infrastructure, and national security markets.