 Search
Search


Risk events such as pandemics, cybersecurity attacks, geopolitical uncertainty, and climate-related weather incidents are driving organizations to review and, if necessary, overhaul their existing supply chain risk management (SCRM) strategies. Add to that increased competition, third-party complexity, supply chain continuity challenges, new business models, and changing regulations, and it’s clear that a robust SCRM program is essential to helping organizations improve operational performance and more effectively manage risks.
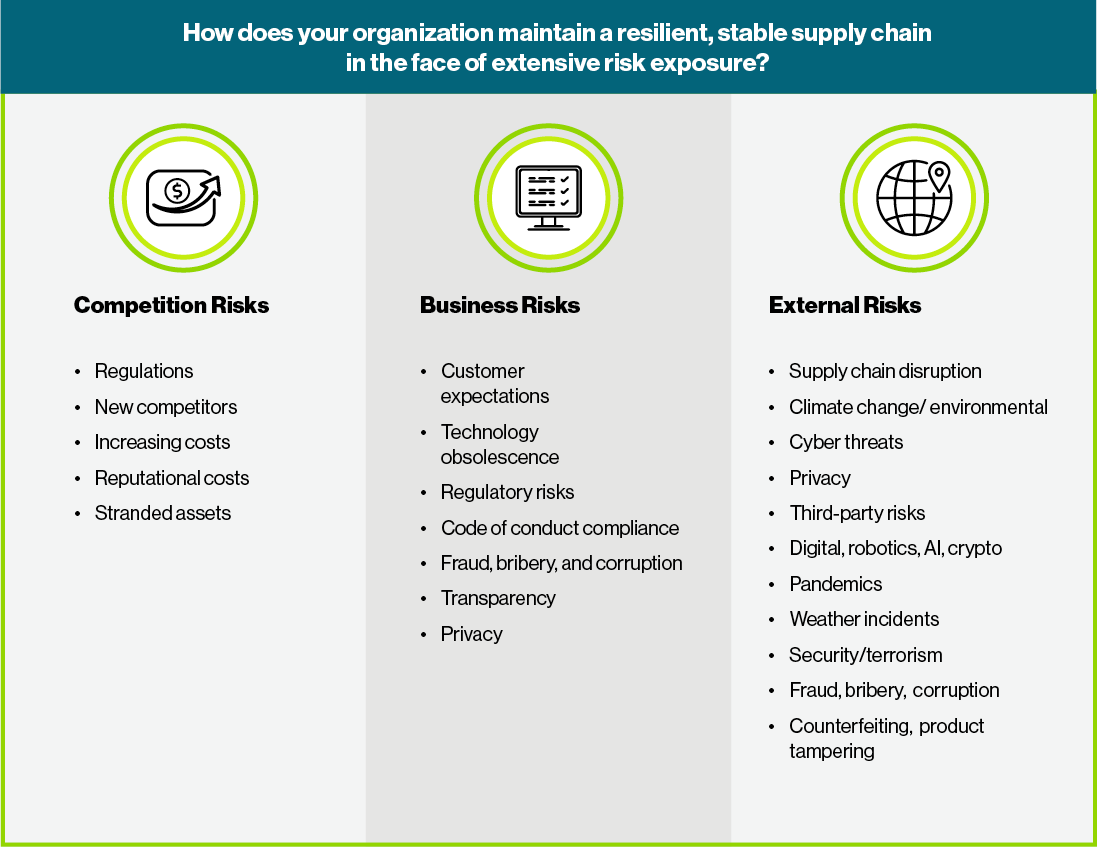
Organizations are faced with significant challenges due to volatile, unpredictable, and vulnerable supply chains.

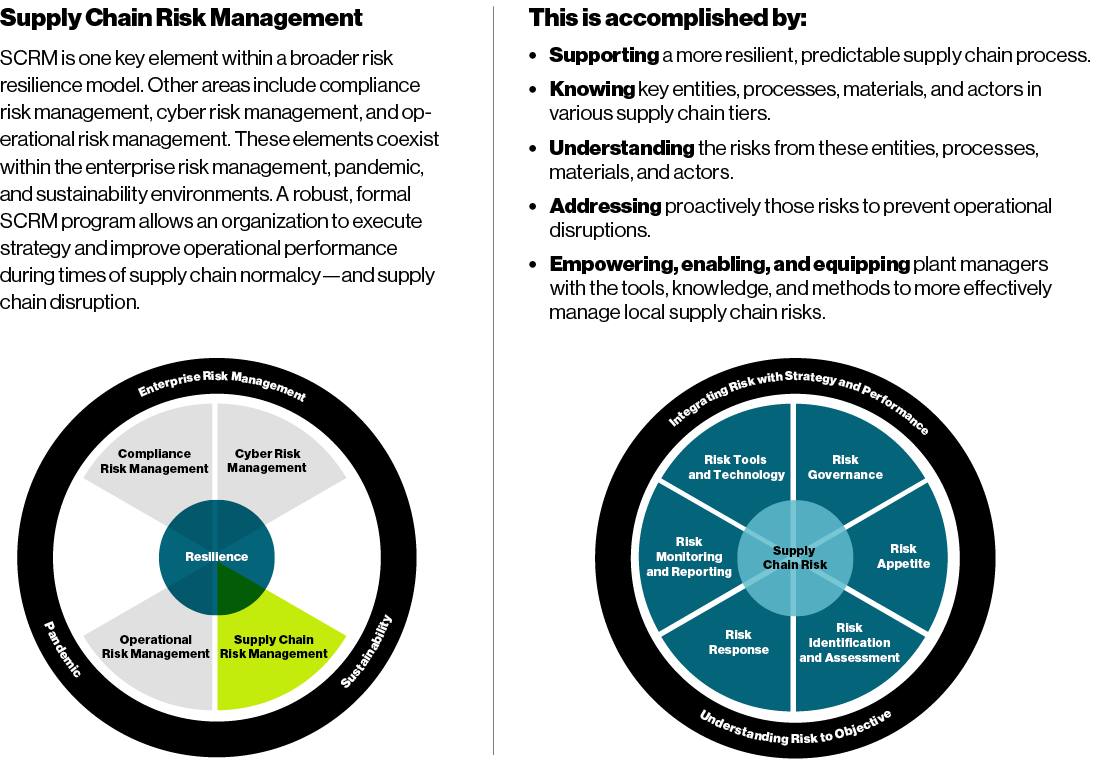
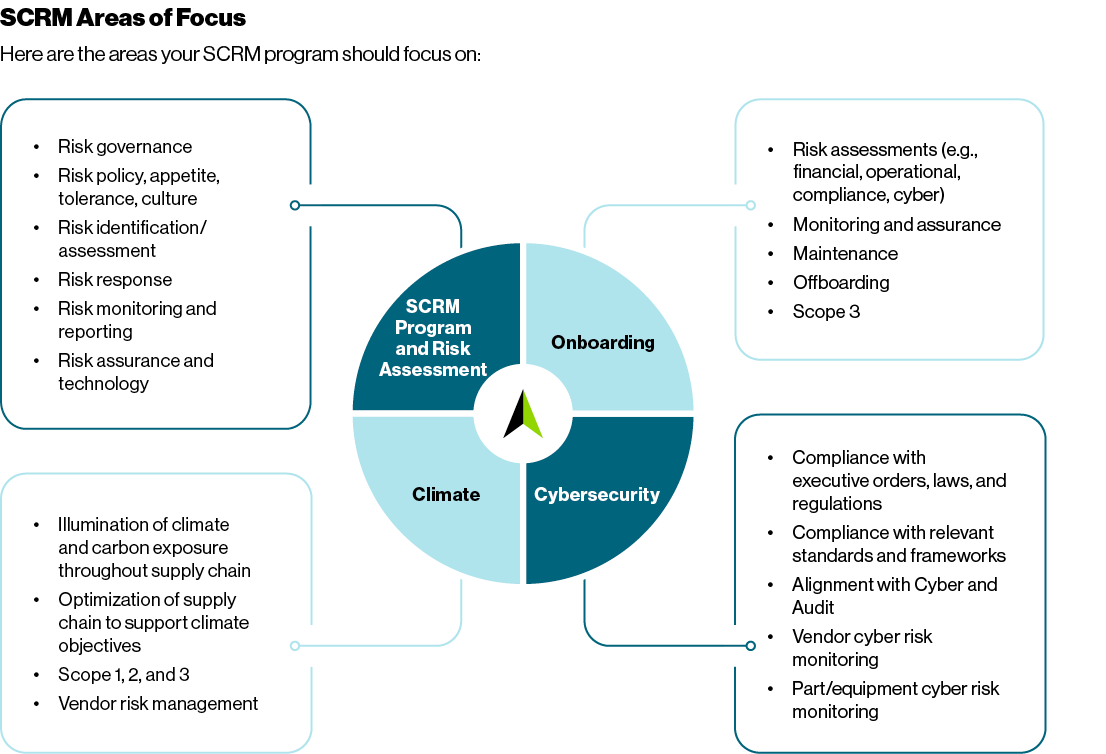
Build — Build a formal SCRM program, based on enterprise risk management (ERM) principles. Our approach includes the following dimensions: risk governance and oversight, risk appetite, risk identification and assessment, risk response, risk reporting/monitoring, risk assurance, and the use of risk technology.
Illuminate — Illuminate and map the supply chain to identify the parties involved, including suppliers, vendors, manufacturers, brokers, freight forwarders, and other service providers—as well as the suppliers’ suppliers. We help clients create a “map” that is as detailed as possible, showing the entire supply chain for the system, component, or product, often to the fifth tier or below.
Conduct — Conduct supply chain risk assessment to determine the risk of third parties with controlling or influential interests, along with their location and associated activity. We work with clients to develop a customized set of risk factors to perform risk assessments on new or existing supply chain providers.
Perform — Perform open-source, commercial due diligence investigations to identify potential threats. Using analytical tradecraft and commercial best practices, our due diligence reviews help identify and verify factors such as beneficial ownership, business reputation, financial well-being, commercial practices, related business activities, business partners, disputes or litigation, USG contracts, relationships with foreign governments or individuals, sanctions or watchlist data, and civil or criminal investigations.
Assess — Assess the strategic impact of potential threats and present results in analytical or other types of reports to the client—specific to its supply chain. In some cases, there may be nothing of concern; in others, we may find adverse or even high-risk information, such as connections to a hostile foreign head of state, cyberbreaches, counterfeiters, substandard parts, or other issues of financial or quality control concern.
Provide — Provide mitigation and remediation recommendations to address vulnerabilities or other deficiencies and threats and work with our clients to implement changes as necessary. For example, we have recommended to some clients that they conduct penetration testing, change suppliers, perform continuous monitoring, enhance common minimum standards, carry out surprise inspections or periodic reassessments, provide referrals to law enforcement or intelligence, or issue warnings about or prohibit certain vendors.
Monitor — Monitor critical and sensitive components and entities continuously. This is increasingly necessary and should be the standard...across the most sensitive parts of key national security- and business-related supply chains. One-time reviews or “snapshots” are no longer adequate. Comprehensive, continuous monitoring and evaluation of suppliers is necessary to inform stakeholders of changes to risks that may arise on an almost daily basis.
Evaluate — Evaluate the vendor management system with Sourcing/Procurement. Ensure it is consistently used across the organization, includes a centralized repository, and possesses the following functionalities: vendor search, invitation, self-service/registration, profile qualification, onboarding, maintenance, offboarding, assuring/testing, performance management, alerts/notifications, reporting/dashboards, security, and workflow.
Review — Review the contract management system with Legal. Ensure it is consistently used across the organization, includes a centralized repository, and deploys the following functionalities: request and intake, search capabilities, contract clauses, template libraries, a hierarchy of all master agreements/amendments/orders, redlining/approval, electronic signature, and maintenance.
Orchestrate — Orchestrate the supply chain. Individual SCRM functions (e.g., sourcing, supplier management, third party risk management, asset protection) need to be effective individually, orchestrated collectively, and integrated with strategy, planning, finance, operations, and other key functions to further create, preserve, and realize value.
Drive — Drive organizational integration. SCRM, cybersecurity, ERM, and other crucial elements of the supply chain often happen in isolated pockets throughout organizations. We help break down internal silos and pave the way for information-sharing and collaboration with internal and, where appropriate, external stakeholders.


Guidehouse is a global AI-led professional services firm delivering advisory, technology, and managed services to the commercial and government sectors. With an integrated business technology approach, Guidehouse drives efficiency and resilience in the healthcare, financial services, energy, infrastructure, and national security markets.