 Search
Search


In today’s increasingly digitized world, cyberattacks are among the most prevalent and dangerous threats to our way of life. Imagine these higher education scenarios: your financial aid disbursement is due tomorrow and students are counting on those funds to pay for housing, buy groceries, or provide a cushion in between paychecks, when suddenly ransomware prevents system processing. Or payroll is processing, and cybercriminals have rerouted direct deposits to their own bank accounts. How would potential students, currently enrolled students, or alumni feel if their personal health information was compromised at the student health facility or posted on the internet?
As repositories of large amounts of data, universities are becoming popular targets of bad actors online. According to S&P Global, there were approximately 1,600 weekly cyberattacks on institutions of higher education in 2021 — one of the highest rates of cyberattack increases compared with other industries.1 Changes in digital infrastructure to support greater information sharing and facilitate spaces of learning, expand the landscape of threats that institutions of higher education face. Universities experience a variety of online threats: phishing of students, teachers, and administrators (and “whaling” of desirable high-impact targets such as registrars and financial aid offices), ransomware, SQL injections, and data breaches are among the most common types of attacks.2 New data sharing policies and changing regulations around the use of cookies and monitoring internet patterns of behavior by institutions also present challenges and new avenues of exploitation from bad actors. Additionally, academic and commercial research is an attractive target in inter-state cyberwarfare, making higher education a new battleground for foreign involvement in the U.S.3
With financial, security, and reputational risks on the line, and an ever-changing threat landscape, research and learning institutions should consider cybersecurity as a key component in their enterprise risk mitigation strategies.
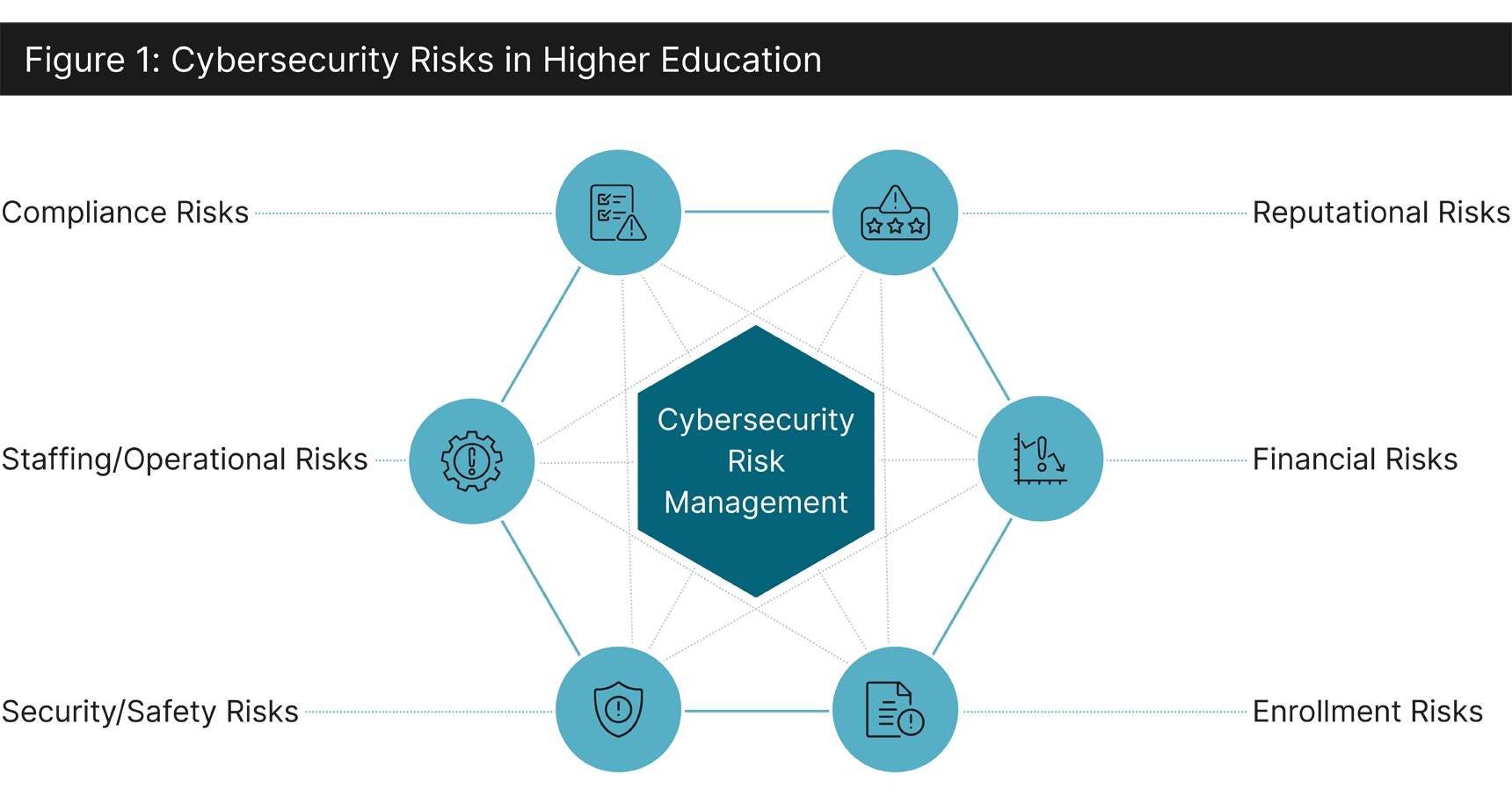
Institutions of higher education have a plethora of assets attractive to bad actors, such as research information and data, financial information, personal/sensitive information of students, including health records, faculty, staff, and alumni, and websites/social media information. Colleges and universities have a duty to safeguard this data for their students, faculty, staff, and others in their user community. Additionally, recruiting efforts for students, donors, and even employees are at risk of denial-of-service attacks when campaigns are done electronically. Illegitimate requests of the system could slow down responses or even disable the system, impacting key interactions like a student application, a donation to the college, or retention of a star faculty member that can command millions in research dollars.
Colleges and universities face a core challenge in cyber risk preparedness: the increasing frequency of cyberattacks, rising costs to combat them (i.e., regular tech updates required), and a lack of buy-in from leadership and system users — all of which create an imbalance in the risk management experience needed to respond to threats. Concurrently, vulnerabilities come from many sources, such as a transient student population that may have a lack of cybersecurity awareness and knowledge (that also generally uses their own equipment) to a lack of management support and resources.4 Research shows that attackers target human nature; meaning an institution’s systems and technology may be state-of-the-art but still subject to human error in a continuously renewing population of students and as vulnerable as human thinking.5 To effectively meet current challenges, cybersecurity needs to be embedded in the overall risk management profile of higher-education institutions and spearheaded by leadership.
In the United States, in recognition of the growing threats to institutions of higher education, the Department of Education and the Department of Homeland Security developed materials through the Readiness and Emergency Management for Schools Technical Assistance Center to provide guidance to institutions of higher education in protecting themselves from cybercrime.6 As detailed in the Guide for Developing High-Quality Emergency Operations Plans for Institutions of Higher Education, a key component of cyber risk mitigation efforts is to create an emergency preparedness plan that emphasizes the necessity of a clear response chain of command, collaborative planning with stakeholders in the academic community, and sharing lessons learned with organizational peers.7
As cyberthreat actors continuously update their tactics and target those slowest to adapt, an awareness of the changing landscape and best practices incorporated by peer institutions is required. Both the Office of Educational Technology at the U.S. Department of Education and the Cybersecurity and Infrastructure Security Agency (CISA) at the U.S. Department of Homeland Security provide guidance on cybersecurity, with CISA being able to facilitate information sharing related to new threats across organizations of different types. This information sharing supports regularly updated intelligence related to new threats emerging in the environment and may be the best defense against groups that capitalize on outdated systems and lack of defined cybersecurity processes.

Cybersecurity risk mitigation can take many forms and it is important for institutions and decision-makers to remain flexible when faced with a cyberattack or developing prevention strategies to ward off cyberthreats. Leaders in higher education can begin by developing and implementing a tailored cybersecurity framework intended to mitigate risk and customized to organizational needs. Utilizing the National Institute of Standards and Technology Cybersecurity Framework8 as a potential benchmark, higher education institutions can decrease their susceptibility to cyberthreats by protecting their networks and data while strengthening their defense mechanism in the event of a cyberattack.
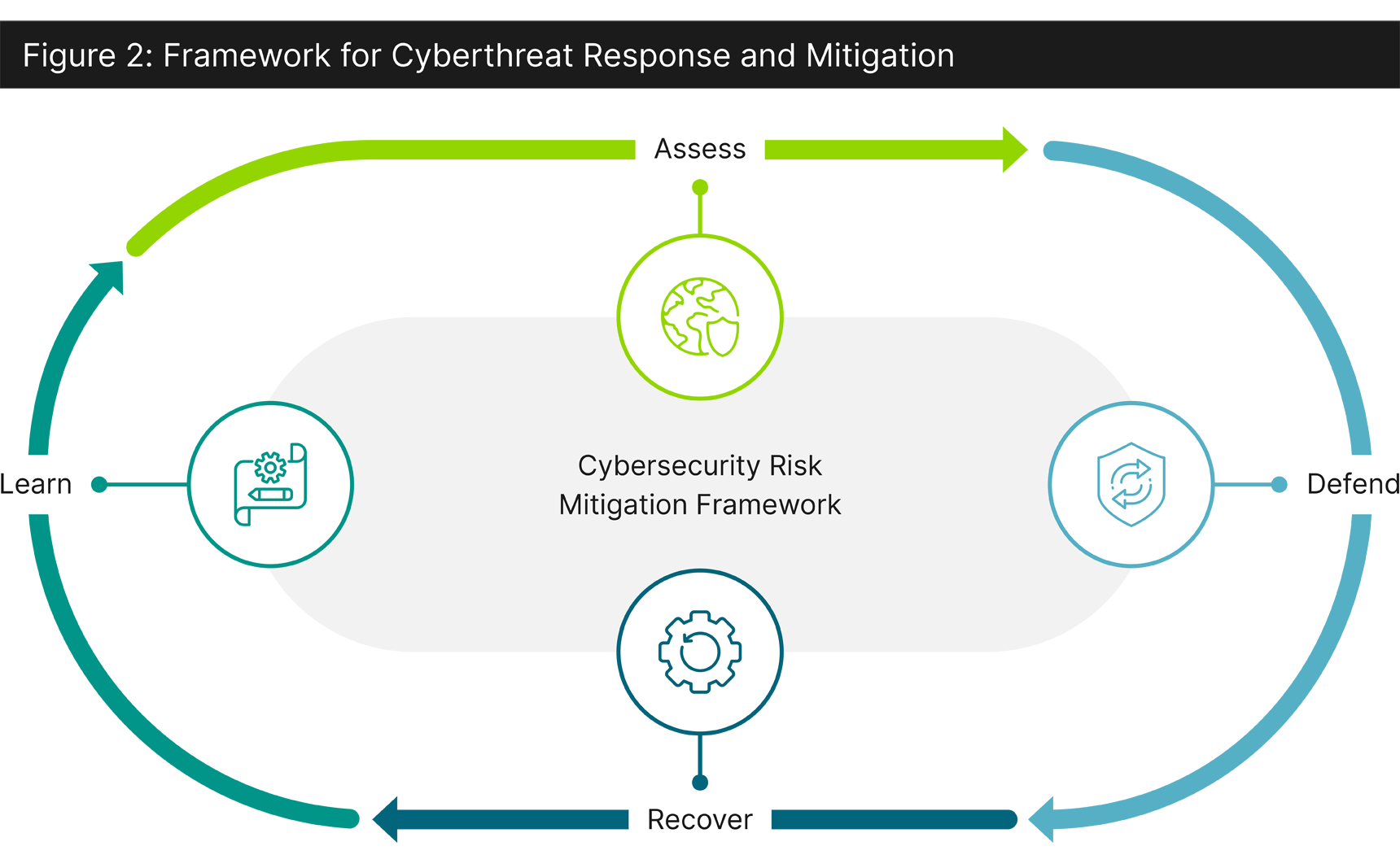
An effective risk management framework will consider an approach to manage vulnerabilities, utilize tactics that can prevent a cyberattack, and enable processes to follow during and after a cyberattack, including the following:
Successfully implementing a cybersecurity risk management framework in higher education involves a skilled Information security team led by a Chief Information and Security Officer (CISO) who can oversee the completion of each stage within the framework. Continuous risk management from a CISO or dedicated professional within the organization is commonplace in large corporations but may be adopted by institutions of higher ed to streamline cybersecurity response activities. Guidehouse can help identify the right resources for developing an information and security function and lead institutions of higher education through the change management processes required to stand up a new office.
Guidehouse cyber consultants help you gather threat intelligence, detect threats, secure your data, respond to cyber breaches, and strengthen identity access management to prepare higher education institutions to mitigate and recover from cyberattacks. We ensure our clients are prepared to address technology risks, both now and in the future. This includes protection of computer systems and networks from information disclosure, theft, and vulnerability to their hardware, software, and electronic data, as well as from service disruption or misdirection in any technology challenges.
This article is authored by David Baskin with contributions Minnie Frye, Adele Brawley, Jasmine McArthur, Stacey Merola.
1 K.W. Rogers, Cyber Risks in a New Era: U.S. Colleges and Universities Go Back to School on Cyber Security Preparedness, S&P Global, 2022.
2 Ashley Lukehart, “Top 5 Cybersecurity Threats Facing Higher Education,” Fierce Education, July 5, 2022, www.fierceeducation.com/technology/top-5-cybersecurity-threats-facing-higher-education.
3 K.W. Rogers, Cyber Risks in a New Era: U.S. Colleges and Universities Go Back to School on Cyber Security Preparedness, S&P Global, 2022.
4 Joachim Bjørge Ulven and Wangen Gaute, “A Systematic Review of Cybersecurity Risks in Higher Education,” Future Internet, vol. 13, no. 2, Feb. 2021, p. 39. Crossref, https://doi.org/10.3390/fi13020039.
5 S&P Global, Cyber Trends and Credit Risks, S&P Global, 2022.
6 Privacy Technical Assistance Center, Protecting Student Privacy While Using Online Educational Services: Requirements and Best Practices, U.S. Department of Education, 2014.
7 GUIDE FOR DEVELOPING HIGH-QUALITY EMERGENCY OPERATIONS PLANS FOR INSTITUTIONS OF HIGHER EDUCATION, U.S., Department of Education, 2014.
8 Holly Vedova and The FTC Office of Technology, “Understanding the NIST Cybersecurity Framework,” Federal Trade Commission, Oct. 6, 2022, www.ftc.gov/business-guidance/small-businesses/cybersecurity/nist-framework.
Guidehouse is a global AI-led professional services firm delivering advisory, technology, and managed services to the commercial and government sectors. With an integrated business technology approach, Guidehouse drives efficiency and resilience in the healthcare, financial services, energy, infrastructure, and national security markets.