 Search
Search


It is estimated that North Korea, the Democratic People’s Republic of Korea (DPRK), has been dispatching thousands of skilled IT workers to fraudulently obtain employment with U.S. IT companies1 as a way to evade U.S. sanctions and fund the DPRK’s Weapons of Mass Destruction (WMD) and intercontinental ballistic missile program.2 Reports estimate that up to 50% of the DPRK’s Gross Domestic Product is derived from sanctions circumvention schemes, predominantly cyber-attacks, digital asset theft, and IT worker fraud schemes.3,4 The threat is not new. The U.S. Department of the Treasury, the State Department, and the Federal Bureau of Investigation (FBI) released a joint advisory detailing the scheme in May 2022.5 Due to recent enforcement actions, the scheme has been receiving increased media attention.
For years, the FBI has been unraveling a scam perpetrated by agents of North Korea. On October 17, 2023, the U.S. seized 17 website domains used by DPRK IT workers in a scheme to defraud U.S. and foreign businesses, evade sanctions, and fund the development of the DPRK’s WMD program.6 Similarly, in May 2024, an Arizona woman was arrested for helping a Ukrainian national and three North Koreans compromise scores of Americans’ identities to facilitate remote work positions for IT workers tied to DPRK. In the same month, the U.S. State Department announced a reward of $5 million for information concerning a criminal network acting on behalf of North Korea for scamming U.S. companies out of $6.8 million.7
This fraud scheme raises profound national security concerns regarding sanctions evasion and critical infrastructure, and it demands a robust compliance response incorporating meticulous risk and threat assessments by IT firms pursuing remote workers and the financial institutions that may be used to transfer and convert fraudulent funds. Organizations should proactively evaluate their risk exposure and consider risk-based mitigation strategies amidst the heightened enforcement activity.
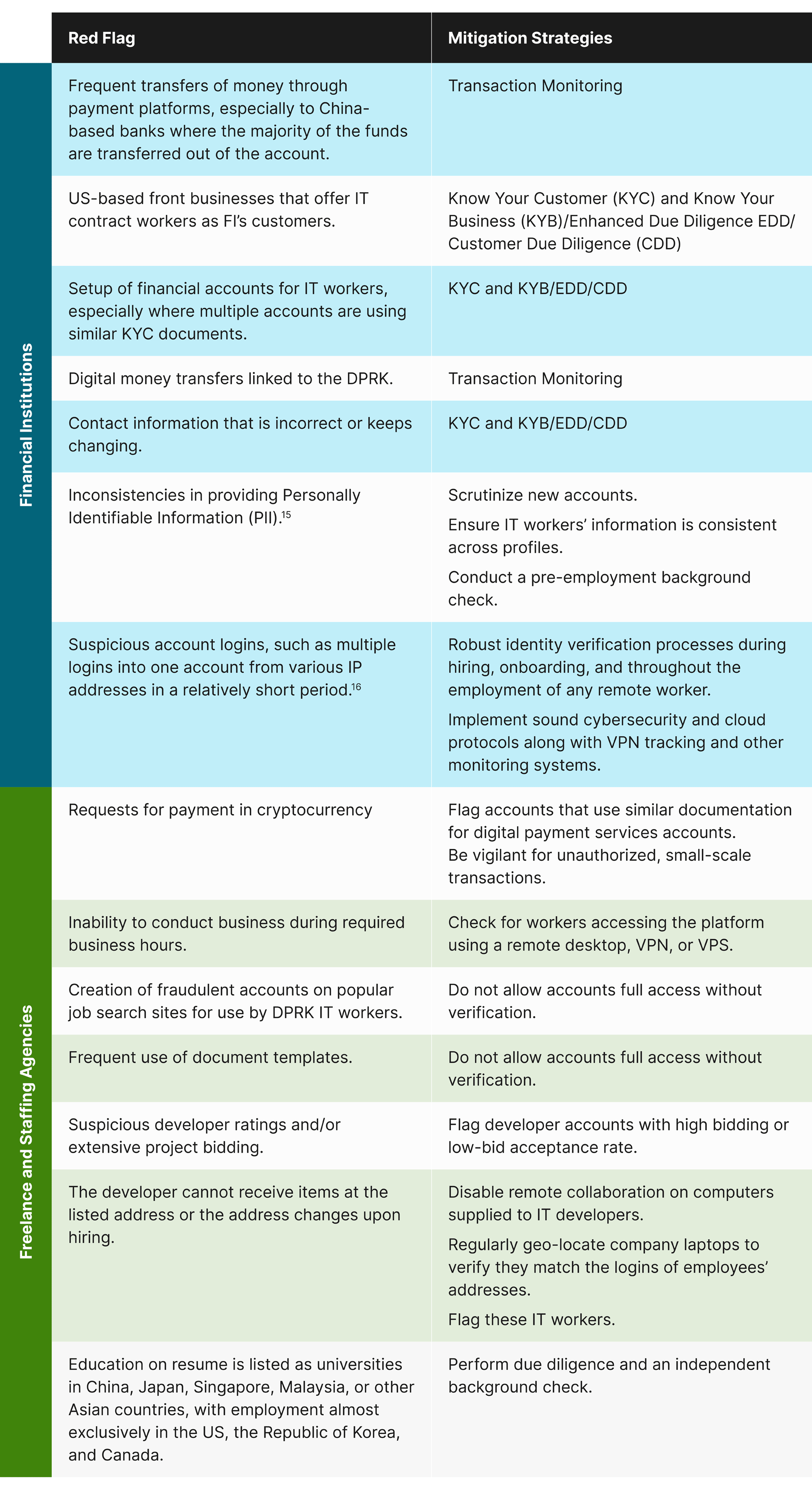
Foreign IT workers live abroad and use fake or stolen names, falsified or stolen documents, fake websites, and misleading IP addresses to pose as U.S. citizens or citizens of other non-sanctioned countries. According to the U.S. Office of Foreign Assets Control, “These employees target employers located in wealthier countries, utilizing a variety of mainstream and industry-specific freelance contracting, payment, and social media and networking platforms.”8
DPRK IT workers purchase access to a proxy account or hire third parties as a proxy to obscure identity. They then submit fraudulent or altered identification and credentials for accounts on freelance work platforms and digital payment services. The client provides equipment to the IT worker once the worker wins a contract from a client on the freelance platform. After the contract is completed, the client processes payments to the DPRK IT worker’s fraudulent account.9
The IT workers also use both witting and unwitting individuals from non-sanctioned countries to gain fraudulent employment and access to U.S. company networks to generate this revenue. These witting and unwitting individuals provide a U.S.-based location for companies to send devices, enabling DPRK IT workers to circumvent controls companies may have in place to prevent the hiring of illicit, overseas workers, as well as controls intended to prevent unauthorized access to company networks by these IT workers, including through the unauthorized installation of remote access software.10
The illicit revenue funds DPRK’s WMD and ballistic missile programs. According to a policy advisor for South Korea’s navy, foreign ministry, and unification ministry, “Pyongyang has crammed more weapons advances in the past five years than during any similar stretch in the country’s history.”11 According to an unclassified report released by the Defense Intelligence Agency, Russia has been using ballistic missiles produced in North Korea in its war against Ukraine.12
The IT workers may or may not engage in any malicious cyber activity while doing their jobs, but they have used the privileged access gained as contractors to enable North Korea’s malicious cyber intrusions.13
The remote DPRK IT workers involved in the intricate fraud schemes may also themselves be victims, as they are subjected to forced labor and close surveillance by government security agents. IT workers have also been forced to work 12-16 hours per day, which may be an indicator of forced labor, abuse of their human rights, and human trafficking.14
The guidance and red flags applicable to your organization depend on the industry and part(s) of the scheme in which your industry is most vulnerable. For instance, freelance and staffing organizations are on the front-lines and risk potentially hiring a fraudulent remote IT worker. Financial institutions (FIs), including banks, cryptocurrency exchanges, and payment processors, are at risk of the workers using their platforms to transfer proceeds ultimately destined for the DPRK’s WMD or Ballistic Missile programs. Financial institutions also expose themselves to similar risks as freelance and staffing firms if they hire remote IT workers.
Guidance and mitigation strategies offered in the various advisories include:
At-risk organizations should develop relationships with the Department of Justice, the State Department, and the FBI early for timely communication if and when incidents arise. They should also involve their legal teams or in-house counsel to inform them about these risks and develop procedures for escalating and reporting suspicious activity to the appropriate agencies.
Attributing suspicious activity specifically to IT worker fraud, as opposed to other common types of fraud schemes, could be a challenge for organizations. Guidehouse experts are at the forefront of this particular fraud trend and can provide detailed training tailored to your organization’s unique risk exposure to help you identify, attribute, and mitigate potential IT worker fraud activity.
Guidehouse is a global AI-led professional services firm delivering advisory, technology, and managed services to the commercial and government sectors. With an integrated business technology approach, Guidehouse drives efficiency and resilience in the healthcare, financial services, energy, infrastructure, and national security markets.